How To Secure MySQL Databases With Encryption
We live in an age of excessive data breaches and unauthorized access in which, as a current data security approach, Securing MySQL databases with encryption has become a vital procedure. MYSQL is a widely employed database management system that can potentially hold sensitive data, including personal info, financial details and user credentials. All of these forms of information, if not encrypted properly, become a victim of theft, compromise or interception. All such mishaps happen to sensitive data when it is either being transmitted or stored on a disk. The encryption of any data adds an extra layer of security; it turns the simply accessible or readable data into indiscernible code, which makes it challenging to access or manipulate by users who are unauthorized. Additionally, executing encryptions with MySQL makes it nearly impossible to understand data and gives access and readability to only those users who have the correct decryption keys attained through proper means. A step-by-step process to secure MySQL databases with encryption is as follows.
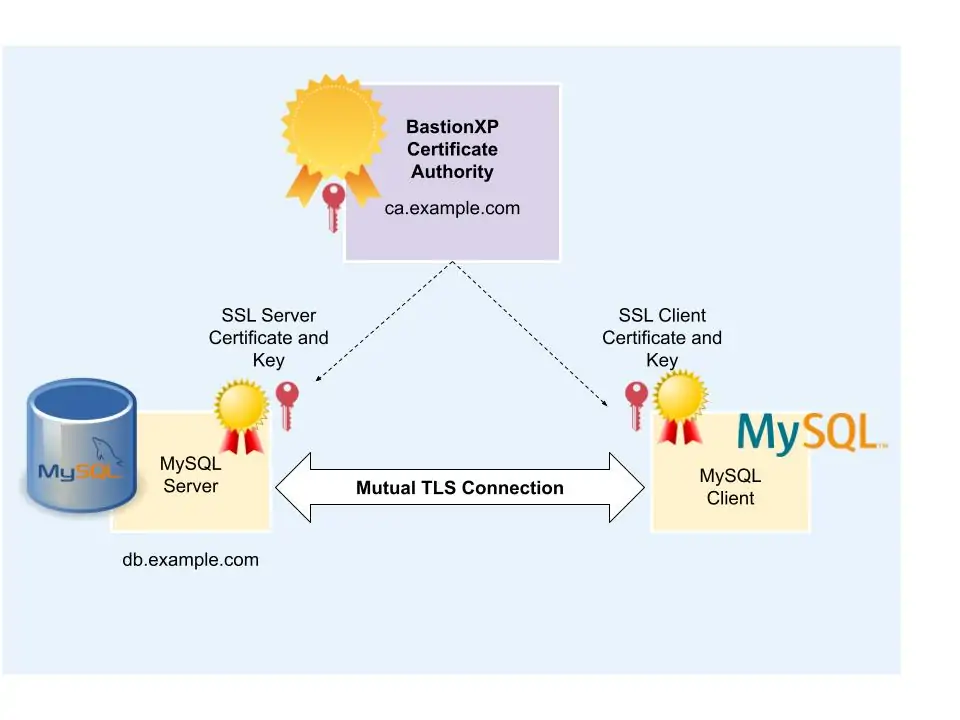
Step 1: Implementing SSL/TLS Encryption In MySQL
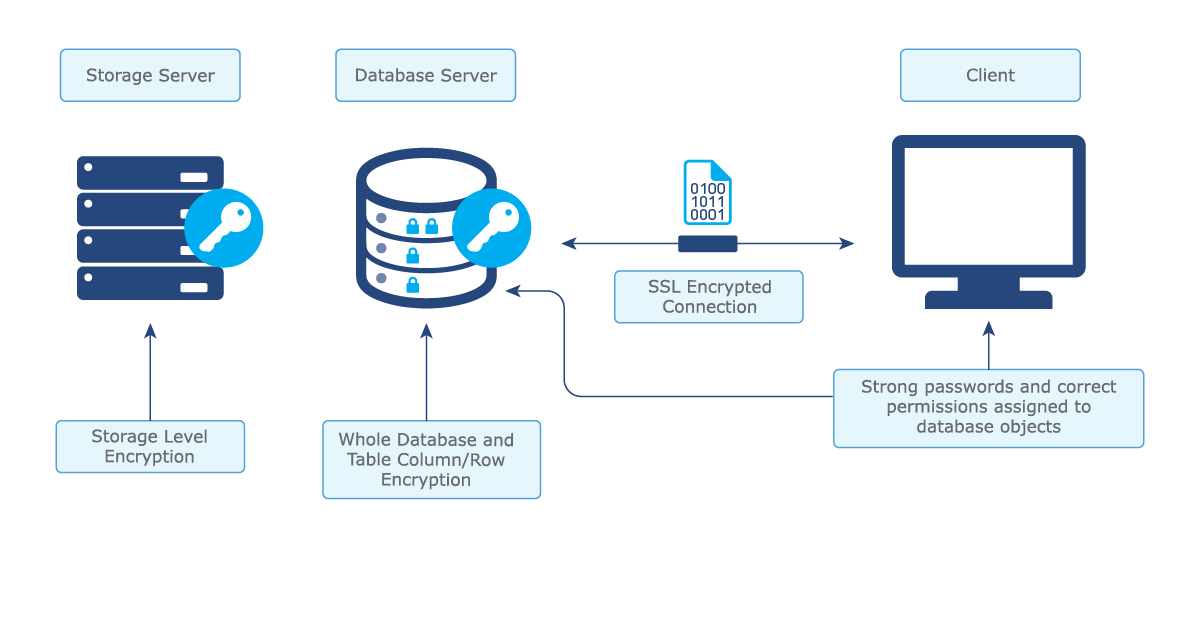
Implementing SSL/TLS encryption in MySQL promises secure communication between the MySQL server and its clients by encrypting information during transmission. Without encryption, information transmitted between clients and the database becomse vulnerable to interferences by attackers, making it effortless for them to grab sensitive data like login credentials and monetary information. By empowering SSL/TLS, you make a secure channel where information is encrypted, essentially lessening the chance of any kind of unauthorized access.
For enabling SSL/TLS in MySQL, you would like to configure the server and clients to utilize SSL certificates. Start by creating SSL certificates utilizing tools such as OpenSSL, then design the MySQL server to utilize these certificates by upgrading the server’s setup file (my.cnf) to indicate the paths for the SSL certificate, key, and CA certificate. Once you have set up the server, confirm that clients also join utilizing SSL by specifying the –ssl-ca, –ssl-cert, and –ssl-key alternatives within the connection string.
You can also get a ssl_mode setting from MySQL that permits you to implement distinctive levels of SSL security. For instance, the REQUIRED mode obliges all client connections to utilize SSL. Correspondingly, VERIFY_CA and VERIFY_IDENTITY modes include extra approval layers for tighter security. This step makes sure that your MySQL connections are encrypted and also prevents eavesdropping and tampering with information in transit.
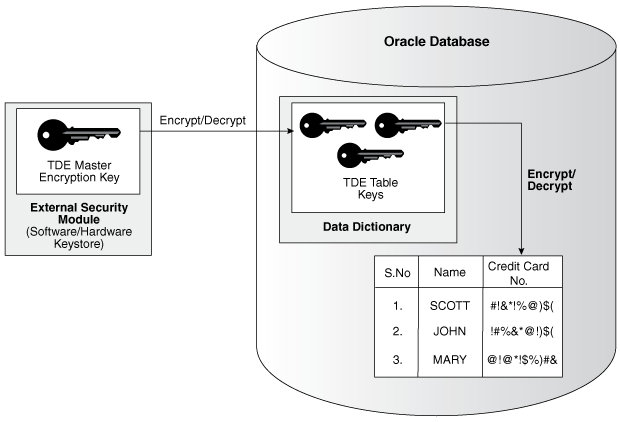
Step 2: Using Transparent Data Encryption For Encrypting Data At Rest
Transparent Data Encryption (TDE) as a MySQL feature secures data-at-rest by automatic encryption of database files stored on disk. It guarantees that even if somebody acquires physical access to your server or storage gadget, they cannot effortlessly read or abuse the information without the right encryption keys. TDE works consistently, suggesting it does not mandate modifications to your applications or queries—encryption and decryption occur automatically in the backdrop.
For excuting TDE in MySQL, you need to empower the InnoDB storage engine, as TDE is upheld by InnoDB tables. The primary step is to configure a key management system (KMS) to safely store and oversee encryption keys. MySQL Enterprise Edition gives a built-in keyring plugin. Otherwise, you can coordinate external KMS arrangements.
After the key management is put up, you can stimulate encryption for individual tablespaces or the complete database. It is often done utilizing the Alter TABLE statement to encrypt particular tables or the Alter TABLESPACE statement for whole tablespaces. Just when encryption is enabled, MySQL will encrypt the data files automatically on disk and decrypt them as required for queries without requiring manual mediation.
Step 3: Utilizing InnoDB Table To Encrypt Individual Tables
Utilizing InnoDB table encryption you can encrypt individual tables inside your MySQL database, with a more fine level of security. This strategy is particularly valuable in case you need to selectively encrypt sensitive tables without encrypting the whole database. With the encryption of tables at the InnoDB level, you confirm that only authorized users who have access to the encryption keys can visit or manipulate the information.
For enabling InnoDB table encryption, at first you should be confirmed that the MySQL keyring plugin is enabled to oversee encryption keys. The keyring plugin safely stores encryption keys and incorporates them with the MySQL server to execute encryption and decryption functions. Once the keying is configured, you can specify that specific tables ought to be encrypted by modifying the table properties.
For illustration, to enable encryption on an InnoDB table, you’ll utilize the Alter TABLE command, as mentioned below:
ALTER TABLE table_name ENCRYPTION = ‘Y’;
In this example, the given command will encrypt the table’s data files on disk while leaving the application logic and query performance unchanged. MySQL can manage the encryption in an automatic way and also the decryption process as information is written and read from disk.
Step 4: Encryption Of MySQL Database Backups
The encryption of MySQL database backups is significant for shielding sensitive data when making duplicates of your data. Backups are frequently a neglected security vulnerability, as they hold complete copies of your database, including possibly sensitive information. In case backups are not encrypted, they can effortlessly be gotten to by unauthorized users if stolen or lost, leading to substantial information breaches.
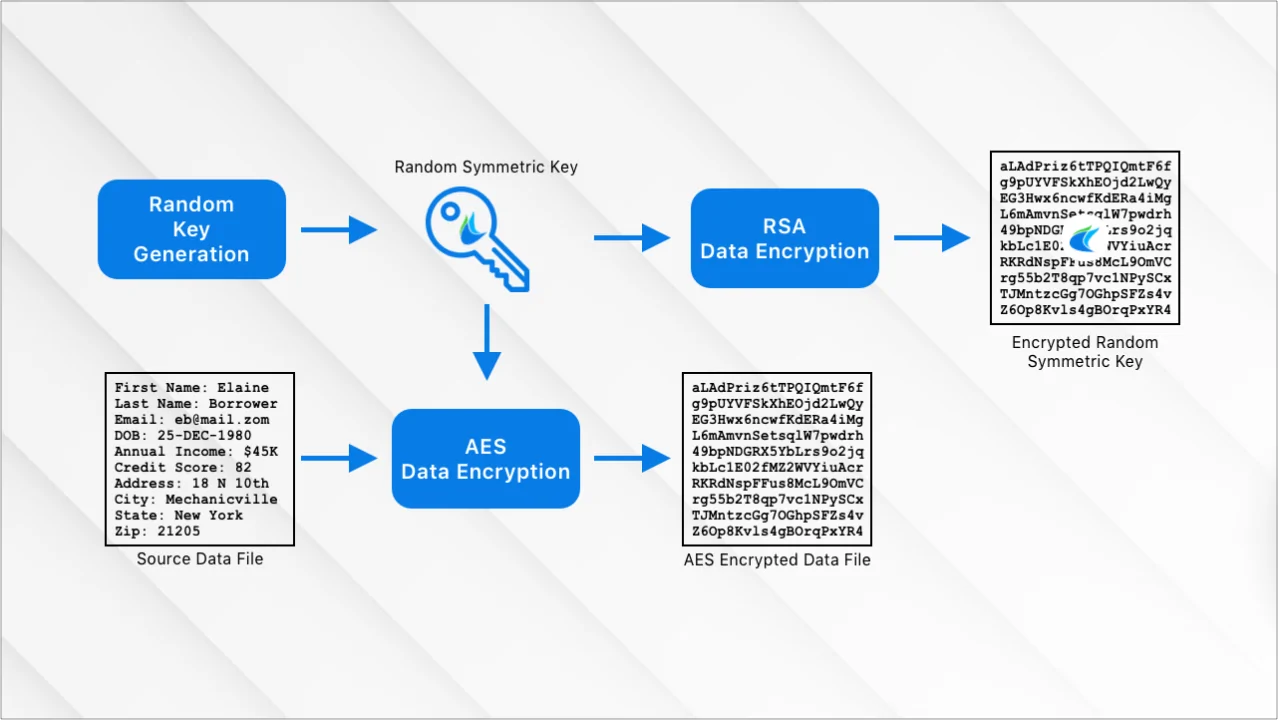
For encryption of backups, you can utilize MySQL Enterprise Backup, which presents built-in encryption functions for backup files. While you are creating a backup utilizing this tool, it lets you specify encryption alternatives to guarantee that the consequent backup file is shielded. You can utilize the given command for encrypting a backup with AES encryption:
mysqlbackup –backup-dir=/path/to/backup –encrypt-algorithm=AES256 –encrypt-key=your_encryption_key backup
The command indicated above can create an encrypted backup file that can only be restored utilizing the right decryption key.
Then again, in case you utilize other backup tools like mysqldump, you’ll manually encrypt the output files utilizing external encryption tools like OpenSSL or GPG. For instance, after creating a backup file with mysqldump, you’ll encrypt it with OpenSSL utilizing the command:
openssl enc -aes-256-cbc -salt -in backup.sql -out backup.sql.enc
The encryption of backups is fundamental for securing database copies amid transfer, storage, or cloud arrangement. This extra level of security promises that even in case a backup is compromised, the information inside stays protected and unreachable without the appropriate decryption keys.
Step 5: Constraining Access To Encryption Keys
Appropriate encryption key administration could be a critical step in securing a MySQL database. Even in case data is encrypted, an unauthorized approach to the encryption keys can cause the encryption to be ineffective. Constraining access to these keys guarantees that only authorized personnel or systems can decrypt sensitive information.
The primary step in restricting access is employing a secure key administration framework (KMS). A KMS assists in storing, producing, and managing encryption keys safely. MySQL gives a built-in keyring plugin for fundamental key management, but you can also integrate external key management arrangements, like AWS Key Management Service (KMS), Google Cloud KMS, or HashiCorp Vault, in accordance with your infrastructure.
While you are setting up your KMS, take these approaches:
Be sure only authorized clients, services, or applications can get to the encryption keys. Utilize roles to allow authorizations, ensuring that only administrators and systems that require the keys for genuine purposes have access.
Frequently observe and audit access to encryption keys. That can help distinguish any unauthorized access tries or abnormal key utilization patterns.
Execute a regular key rotation arrangement to intermittently substitute encryption keys, which diminishes the chance of keys being compromised with time.
For improved security, use hardware security modules to store encryption keys in a physically secure, tamper-resistant device.
Step 6: Auditing Access To Encrypted Data
Observing and auditing access to encrypted information may be a pivotal step in keeping up the security of your MySQL database. Indeed, with encryption input, it’s important to keep note of who gets to encrypted information, when it is accessed, and how it is utilized. This step helps identify likely security breaches, unauthorized access attempts, or unusual patterns of information utilization that may show a compromise.
To execute monitoring and reviewing for encrypted information, consider the following activities:
Utilize MySQL’s audit logging highlight to record all database activity, including getting encrypted information. This log traces who gets to the database, the queries they perform, and any modifications made to encryption settings. These logs ought to be stored safely and surveyed regularly for fishy activity.
If you’re employing a key management system (KMS), guarantee that access to encryption keys is logged and checked. Unauthorized or unforeseen access to encryption keys may be an indication of a probable security breach.
Enforce real-time checking tools that trigger alarms when abnormal designs, like multiple failed access endeavors or unforeseen decryption requests, are recognized.
Occasionally examine database access logs, encryption settings, and key utilization to confirm that your encryption methods are working accurately. These reviews offer assistance in distinguishing any vulnerabilities or shortcomings that may have arisen.
Scanning and reviewing give a visionary layer of security by guaranteeing that any suspicious action is recognized and tended to rapidly. It helps keep up the astuteness of your encryption practices and fortifies the overall protection of your MySQL database.
Conclusion
In summary, data breaches have become a prevalent occurrence within various organizations. These hacks have the potential to be disastrous, leading to large monetary losses, harm to one’s reputation, and possibly legal implications. Tragically, being the foundation of numerous vital applications, MySQL databases, one of the most widely used relational database management systems, are very vulnerable to such assaults. It may seem unlikely, but it is imperative that you take preventative steps to safeguard your MySQL databases. The steps indicated above are meant to fortify your MySQL setups. Additionally, you can use these essential security guidelines to safeguard sensitive data and lower the likelihood of data breaches.