Top 10 Web Application Security Practices You Must Know
We live in an exciting AI century, where almost everything is available at our fingertips. Numerous AI applications are being introduced to make our lives much easier.
However, with such ease comes great responsibility – a dire need to know and understand security practices.
Your web applications may serve as the gateway for operations, like conducting transactions, managing sensitive information, governing user experience, etc.
According to a 2021 research conducted by Positive Technologies, 98% of web applications are prone to vicious attacks from cybercriminals resulting in malware. This can even lead to redirects to malicious websites and much more.
These are vulnerable to a myriad of malicious threats that can blast through the thick veil of the Internet. A company may risk financial losses, reputational damage, and possible prosecution if it ignores the security of its web application.
The best workaround to this solution is to embed an SSL certificate on your website to protect your online operations. The good news is that implementing an SSL certificate is not a tough thing.
If you are worried about the cost involved, you can even opt for cheap SSL certificates equally potent in safeguarding your online properties.
However, the process of making a safe web application differs from the application of a one-time fix. It is a repeated trip of defining what is unsafe and how to navigate the acutely evolving online threats.
10 Web Application Practices Developers Should Know
Here are ten web application practices every developer should know:
#1. Documenting Software Changes
Keeping up to date with the ever-changing situations is only possible with an exhaustive web application evolution journal.
This implies documenting every update, modification, and new adoption of frameworks or libraries.
This comprehensive documentation not only provides swift and direct direction in finding and correcting security breaches but also plays a crucial part in maintaining the long-term security of your application.
It maintains the history of your application’s building process. It lets you review the series of vulnerabilities and see the consequences of each change in your current security position.
#2. Identifying Potential Hack Points
Carefully analyzing your web application to identify modules prone to threats is essential for security.
You can smartly allocate security resources when you classify your software, ranging from the most dangerous areas, such as login screens and transaction pages, to the least critical ones.
This concentrated methodology ensures that the most vulnerable parts of your app are afforded the highest level of protection, preventing unauthorized access and data breaches.
Through this tactical treatment, you build a strong defence line and establish conscientious protection layers where they are most significant.
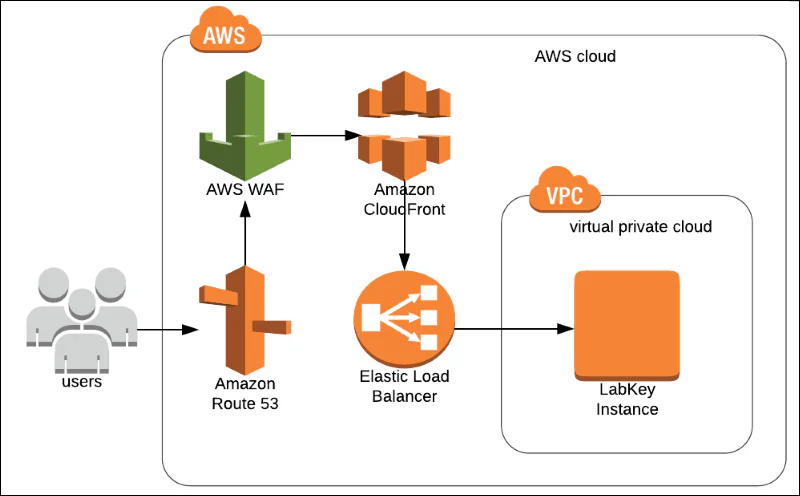
#3. Deploying a Web Application Firewall (WAF)
A Web Application Firewall (WAF) is the first line of defense deployed between the web application and outside vulnerabilities.
WAFs are the gatekeepers that stop malicious traffic from accessing your web application. They significantly contribute to your web security architecture without patching a single line of software code.
Sophisticated WAFs provide multiple-layer security against threats like SQL injections, XSS, and DoS attacks.
#4 Ensuring coding practices
Do you know that the most popular reason for vulnerabilities, misconfiguration, and loopholes is insecure coding practices? Yes, developers may be excited about quick app delivery rather than understanding the security implications of their open-source codes, resulting in flawed code. This can impact a business negatively.
If you are still only looking for design, user experience, or speed, you should look at security measures that need to be taken before anything. Developing features such as authentications, plugins, themes, etc, is important. So, make sure next time you develop a web application, you take security measures at the top of anything.
#5. Leveraging SSL Certificates
All big, small, or mid-size companies must install an SSL certificate for web applications. It can assist companies in accessing browsers by providing relevant details to the end-users.
It helps data transmissions get encrypted with the 256-bit encryption algorithm, which is necessary today.
On top of this, installing an SSL certificate can provide additional protection that discourages potential hackers from stealing your confidential online information during transmission.
A good SSL certificate ensures that only legitimate systems interact with your website. It also aids you in syncing your web app with HIPAA, HITECH, and PCI-DSS standards.
This will ultimately positively impact safeguarding your medical, financial, and other private data related to your business.
While finding a good SSL certificate provider, look at your business requirements regarding online transactions and then determine the best SSL certificate according to your requirements.
If cost is a determining factor, you can get many affordable SSL certificate providers online. However, ensure you do not compromise on the quality while trying to get a cheap SSL certificate. Properly integrating security considerations during the development phase, especially when using various frameworks, is paramount. Frameworks like Angular provide robust structures for building web applications. Utilizing Angular UI components not only helps in creating responsive and dynamic interfaces but also ensures integration with modern security practices. It is crucial that developers focus on the secure implementation of these components to leverage their full potential without exposing vulnerabilities.
#6. Regular Penetration Testing (Ethical Hacking)
Simulating these attacks on the web app is known as penetration testing or ethical hacking, which shows the security holes.
This not only adds another layer of security but also helps you to identify the weak points before malicious actors have the chance to exploit them.
Continuous penetration testing will strengthen your defenses and provide insights into the effect of your current security strategies.
This may appear to be a passive technique. However, it is actually a proactive strategy to find and shut down loopholes before they can be continuously exploited.
#7. Keeping Everything Updated
It is critical to ensure that the web application you set up and all the third-party components involved are updated to the latest security versions. Hackers use known flaws in software that is no longer updated as their gateway.
Keeping your application and its libraries fresh can also help you to cover the vulnerabilities, ensuring no data breaches.
This procedure starts with auditing your utilization of third-party libraries, eliminating excess ones, and updating the rest to the most secure versions.
It can prevent future threats by successfully applying available updates and patches that enable the system to identify known risks and build a robust defence system.
#8. Safeguarding Cookies
The cookies play a central role in web ecology and improve user experience by customizing content, keeping users’ profiles, and implementing high-speed site performance.
Without an acceptable way to manage cookies, they may be as effective as entry points for security weaknesses, such as cookie theft or session hijacking.
· Avoid Storing Sensitive Information in Cookies: Information like passwords, credit card digits, and social security numbers, even in encrypted form, can never be stored in cookies.
· Implement Strict Expiration Policies: A time limit set for short expiration reduces the life space for attackers to leverage the cookies that are transferred or captured in the network.
· Secure Cookies with Encryption: SSL or TLS secure protocol can and should encrypt the entire communication channel between the user’s browser and the web server, including cookies.
· Utilize HttpOnly and SameSite Attributes: The setting of the HttpOnly attribute on cookies commands the browser not to provide client-side scripts access to the cookie. Setting the SameSite to prefer non-cross-site requests could also limit how cookies are sent with web requests.
#9. Real-Time Monitoring
Visualize having a security system comprising an army of vigilant guards who conduct their duties accordingly and alert you whenever there is abnormal activity. The monitoring systems influence real-time controls in the same way as in the virtual setting.
Regular monitoring is one of their key responsibilities. They look for indications of intrusion into your web application and provide useful insights for immediate response.
By rapidly identifying security flaws while they happen, you can stop the infringement from spreading and take action to prevent the threat completely.
#10. Educating Your Team
Security doesn’t just have the technical aspect; it is a requirement everyone should strive for. Every member of your team, from coders to marketers, must be made aware of it.
Create a security awareness doctrine where each member can contribute, thus comprehensively restoring the security of your digital assets.
By getting your workforce involved in training and instigating responsible habits, you have the human firewall against cyber-attacks.
Conclusion
The easy adoption of SSL certificate accessibility is a crucial step toward web security and the chance given to all businesses and websites to secure their online standing confidently.
Affordable SSL certificates confirm that encryption is not only within the reach of large companies alone but a standard that should be universally employed online for privacy and safety issues.
Alongside the ever-changing digital space, adopting SSL certificates will continue to be the pillar of web application security since it guards against cyber threats.